Sneaky-Creeper Social Media C2
Modern enterprises rely on third-party cloud services extensively. Do you monitor data uploaded to them? This trust can be abused to smuggle critical business data past perimeter defenses. Instead of building and maintaining custom infrastructure to control malicious software, attackers can simply rely on legitimate third parties to transport their data for them.
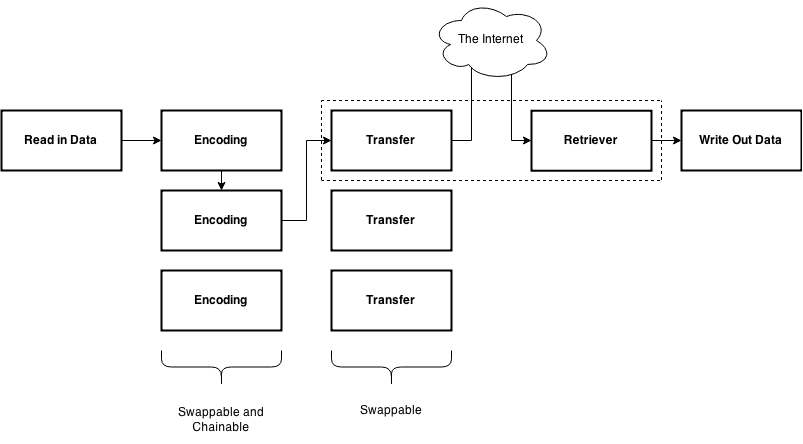
Sneaky-creeper is an open-source project that allows security professionals to emulate the tactics of these advanced adversaries quickly and without expensive custom tools. Its permissive license and modular design allow for the easy addition of additional transport methods to tailor an assessment for your unique requirements.
Project link: https://github.com/DakotaNelson/sneaky-creeper